Secrets, certificates, and access management on autopilot.
All-in-one platform to securely manage application secrets, certificates, SSH keys, and configurations across your team and infrastructure.




Secrets Management
Centralize application secrets across environments and workloads. Enforce identity-based access, auditing, and secure delivery at runtime.
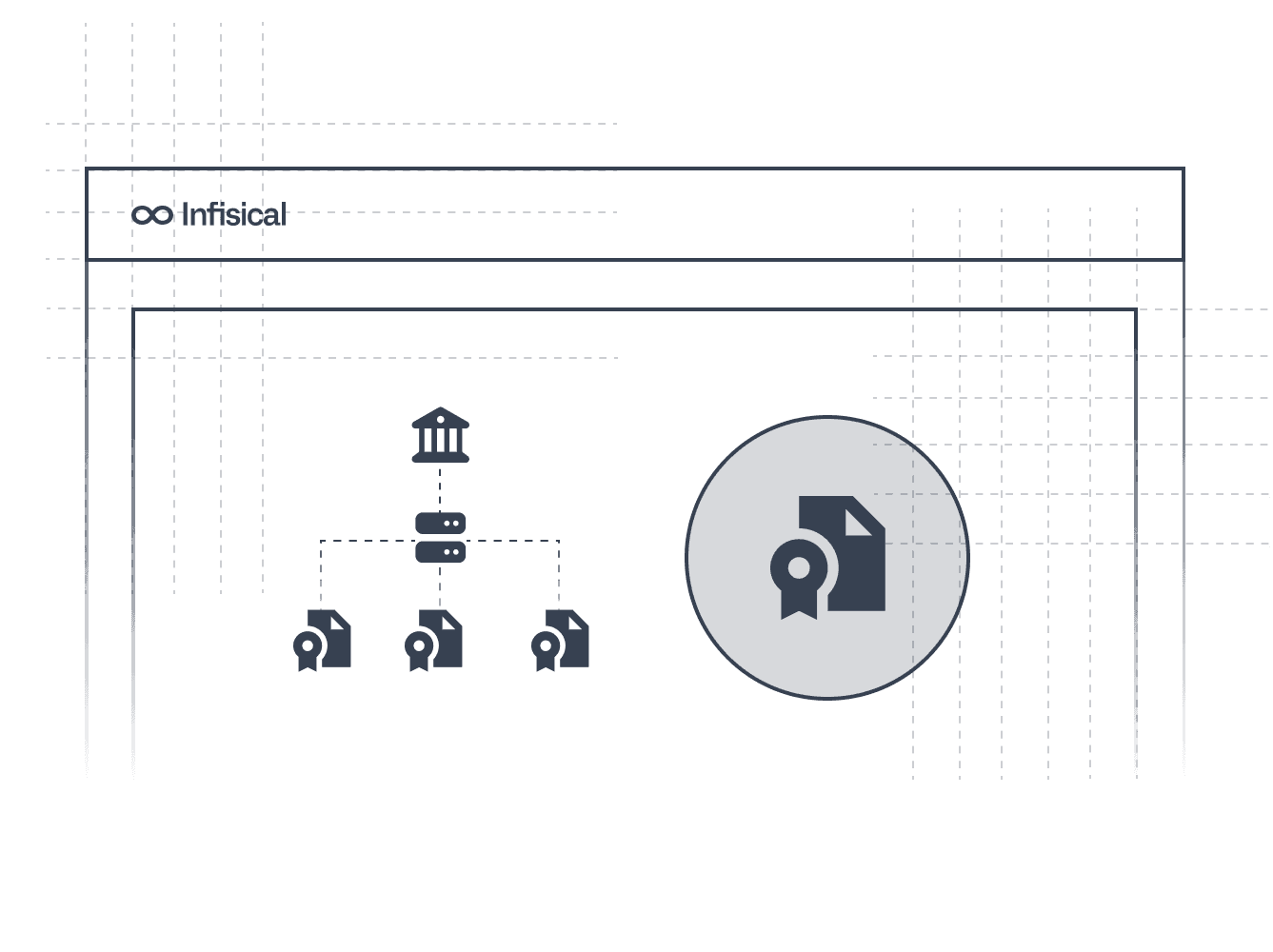
Certificate Management
Centralize certificate lifecycle management across your infrastructure. Automate issuance and renewal operations to eliminate expiration risk across internal and external PKI.

Privileged Access Management
Grant privileged access to infrastructure and sensitive systems only when needed. Enforce just-in-time access with identity-based policies and full auditability.
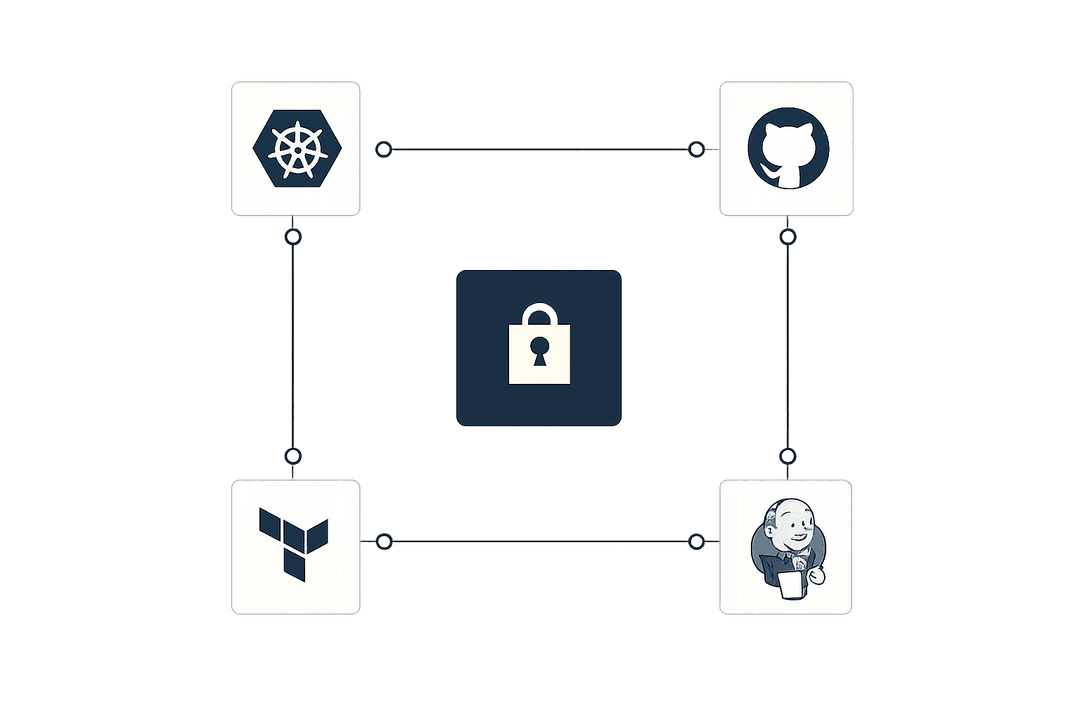
Secrets Management across Infrastructure
Manage secrets across all of your infrastructure – from Kubernetes and Terraform to CI/CD pipelines and local development -- both on-prem and in the cloud.
Dynamic Secrets & Secret Rotation
Eliminate long-lasting credentials to reduce risk of breach and credential leaks. Generate secrets dynamically on-demand in a way that is unique to every client.
Agent Sentinel
Govern how AI agents access tools and external systems. Centralize authentication, policy enforcement, and visibility across MCP endpoints.
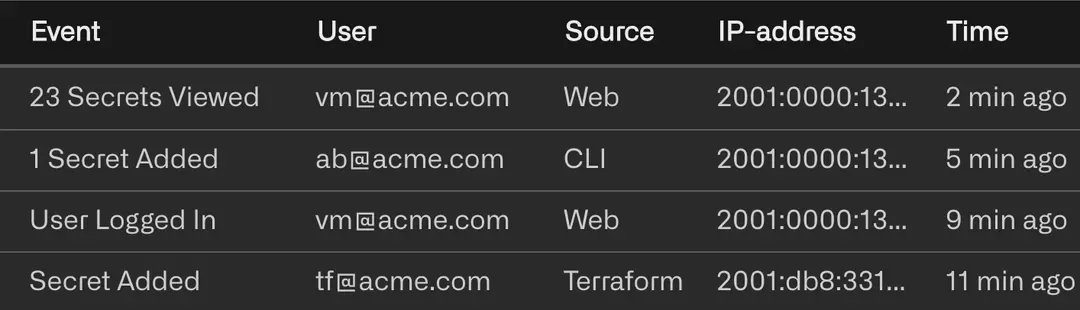
Audit Logs
Track everything. Be aware of every action that is happening to your secrets and other sensitive data.
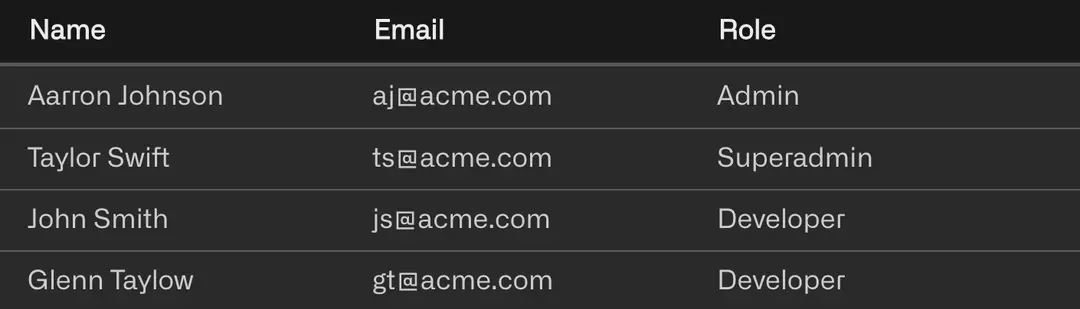
Access Controls
Stay in control. Set up tight granular permissions for human and machine identities.
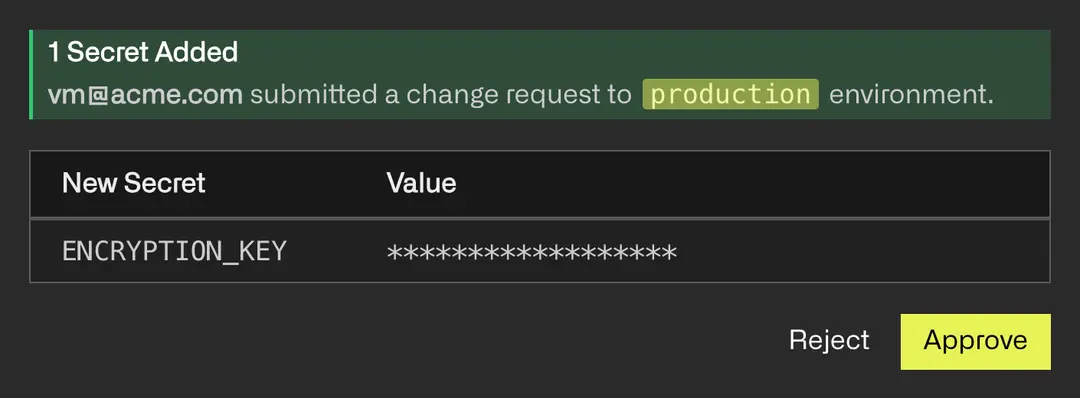
Approval Workflows
Review sensitive changes. Just like in git, assign reviewers to approve secret changes before propagating to apps.
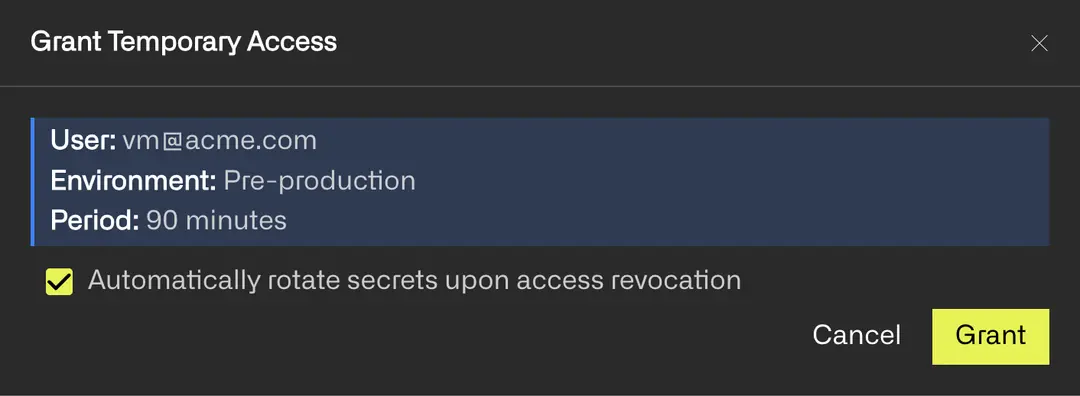
Temporary Access
Trust minimally. Give access to sensitive resources only temporarily. Revoke automatically upon expiration.

Compliant
Infisical is SOC 2, HIPAA, and FIPS 140-3 compliant and is constantly undergoing continuous penetration testing.
Reliable
Powering mission-critical infrastructures of all sizes, with support SLAs and observability.
Secure
Infisical encrypts secrets with AES-GCM-256, enforces tight authentication policies, and more.
Self-hostable
Deploy Infisical on your own infrastructure or use Infisical Cloud with no maintenance overhead.

PRODUCT
CONTACT






























